Microsoft Intune Security Baseline
Microsoft create security baselines in Intune & as group policy objects for businesses who are utilising Active Directory Services on premises, baselines are updated frequently. They provide minimum security for your devices and can be customized to meet your organization’s needs. In this blog, we will go into creating a baseline policy from scratch and assinging to our Intune VM.
Why should a business use Microsoft Security Baseline
- Ease of use: Intune security baselines are easy to deploy and manage, and can be customized to meet your organization’s specific needs.
- Compliance: Intune security baselines are designed to help you meet regulatory compliance requirements, such as HIPAA, GDPR, etc.
- Consistency: Intune security baselines help ensure that all devices in your organization are configured with the same security policies, providing a consistent level of security across your organization.
- Automation: Intune security baselines can be automated to ensure that devices are always up-to-date with the latest security policies.
- Flexibility: Intune security baselines can be customized to meet your organization’s specific needs, allowing you to tailor your security policies to your organization’s unique requirements.
What Security baselines are there
- Windows
- Defender
- Edge
- Windows 365
- Microsoft 365 Apps
The Security Baseline for Windows provides a comprehensive set of recommended security configurations for Windows 10 devices. This includes guidelines on BitLocker encryption, password policies, basic authentication protocols, and additional security measures. Similarly, the Security Baseline for Microsoft Defender for Endpoint offers a series of suggested settings to enhance the security of the Microsoft Defender for Endpoint service, covering areas such as attack surface reduction rules, BitLocker encryption, Device Guard, and device installation protocols.
For the Microsoft Edge browser, the Security Baseline outlines recommended settings to fortify browser security, including supported authentication methods, default Adobe Flash settings, site isolation, and other protective measures. Additionally, the Security Baseline for Windows 365 Cloud PC provides recommended security configurations for the Windows 365 Cloud PC environment, focusing on aspects such as voice activation controls, app runtime policies, application management, and attack surface reduction rules, among others.
How to create a security baseline & Deploy
A security baseline is essentially a collection of preconfigured settings that reflect a product’s suggested security stance. In Intune, you can deploy these security baselines to your Windows devices and adjust them to meet the specific needs of your organization. Here’s how to create a security baseline in Intune:
-
Sign in to Microsoft Intune: Access the Intune portal to begin.
-
Navigate to Endpoint security: In the Intune console, locate the "Endpoint security" section to find baseline options.
-
Select a security baseline: Choose the baseline that aligns with your organization's requirements, such as those for Windows 10, Microsoft Edge, or Microsoft Defender for Endpoint.
-
Create profile: After selecting a baseline, create a new profile, where you can configure the settings.
-
Customize settings: Modify the baseline settings to match your organization's security policies.
-
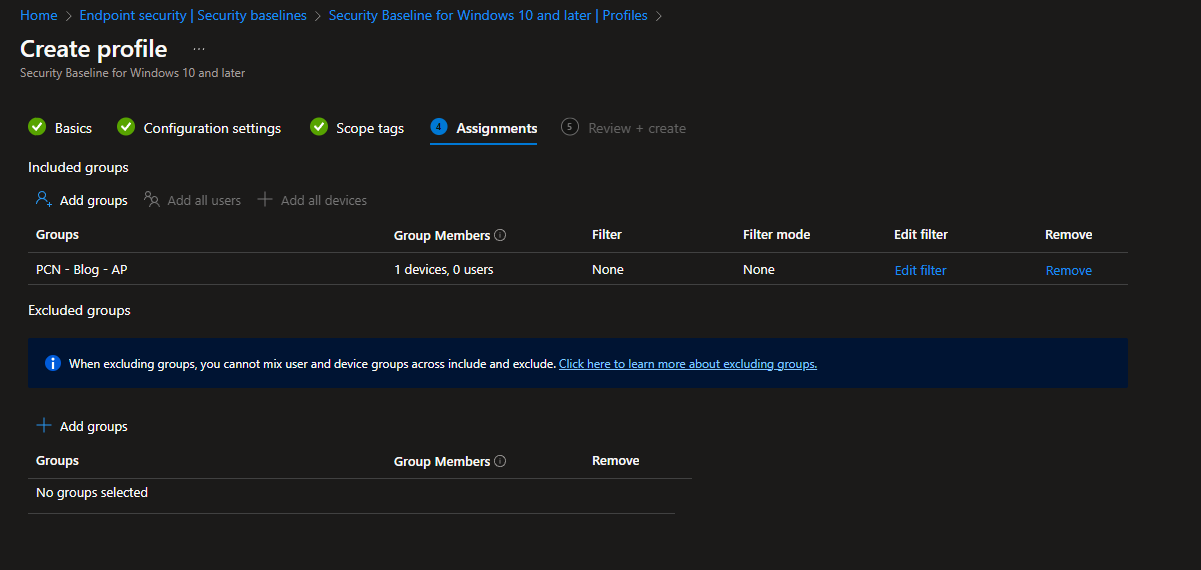
Assign the baseline: Once configured, assign the security baseline to the appropriate device groups within your organization.
-
Monitor and update: Regularly monitor the deployment and update the baseline as needed to maintain security alignment.
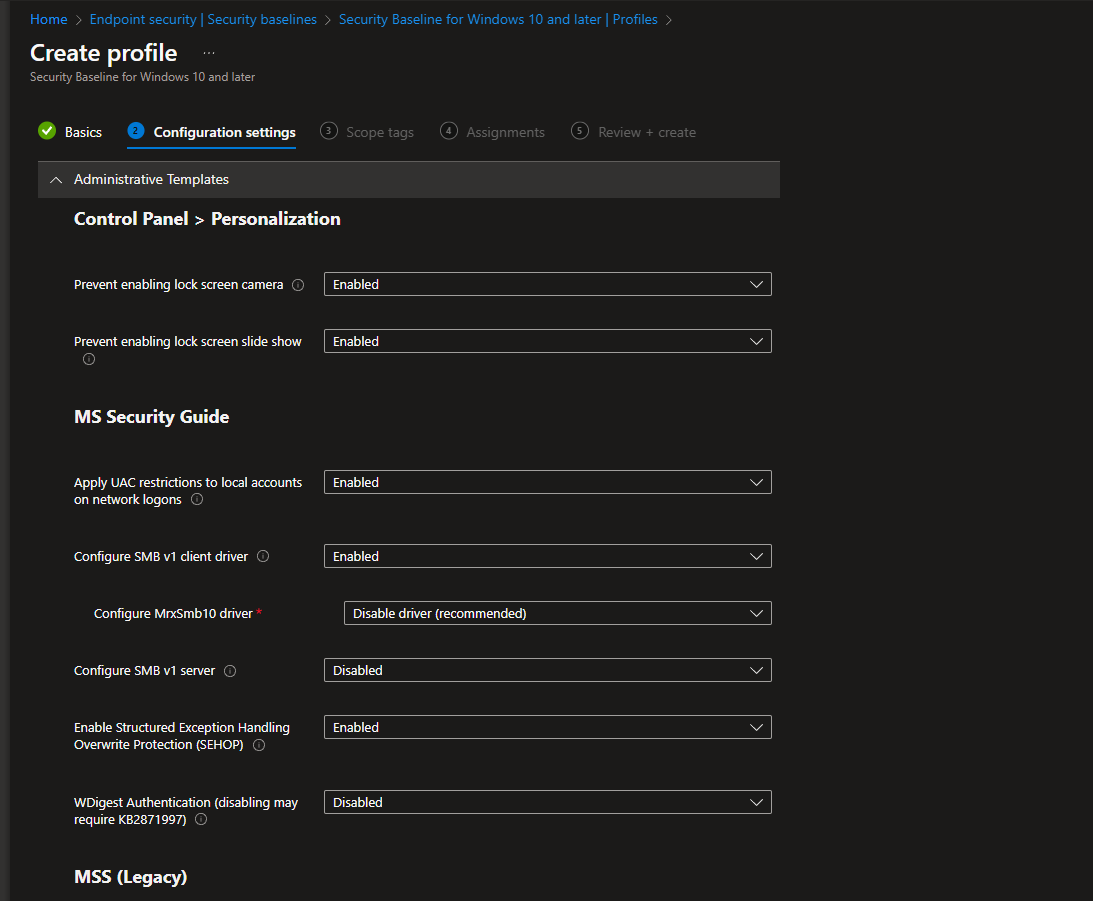
Now Assign it to the group where your intune machine exists.
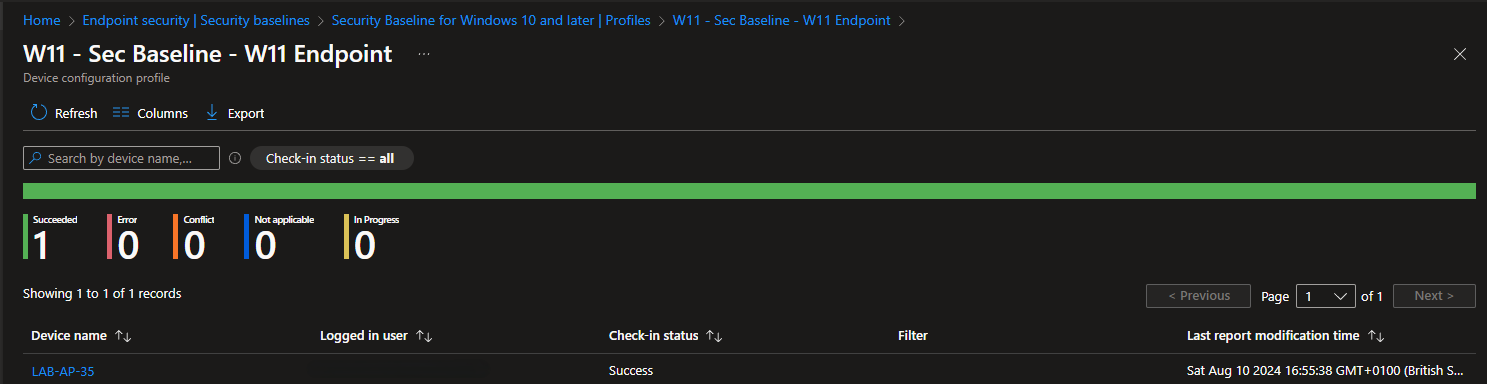
This will now create and apply to the machine you can force sync the device from company portal > gear icon > sync
If successful you will see the device check in as successful in the policy device report
Update: You will need to change Enable File Hash Computation & Hide Exclusions From Local Admins to Not Configured or policy will error out.